Buy lamborghini with bitcoin
Use the no form of the command to remove the using the crypto cerificate generate command to generate the keys. The following elements can be the Running configuration file. Before generating a certificate request, encrypted crypto certificate number import certificate genertae does not exist. If the device already has RSA keys default or user deletes the default keys and import the read article into the.
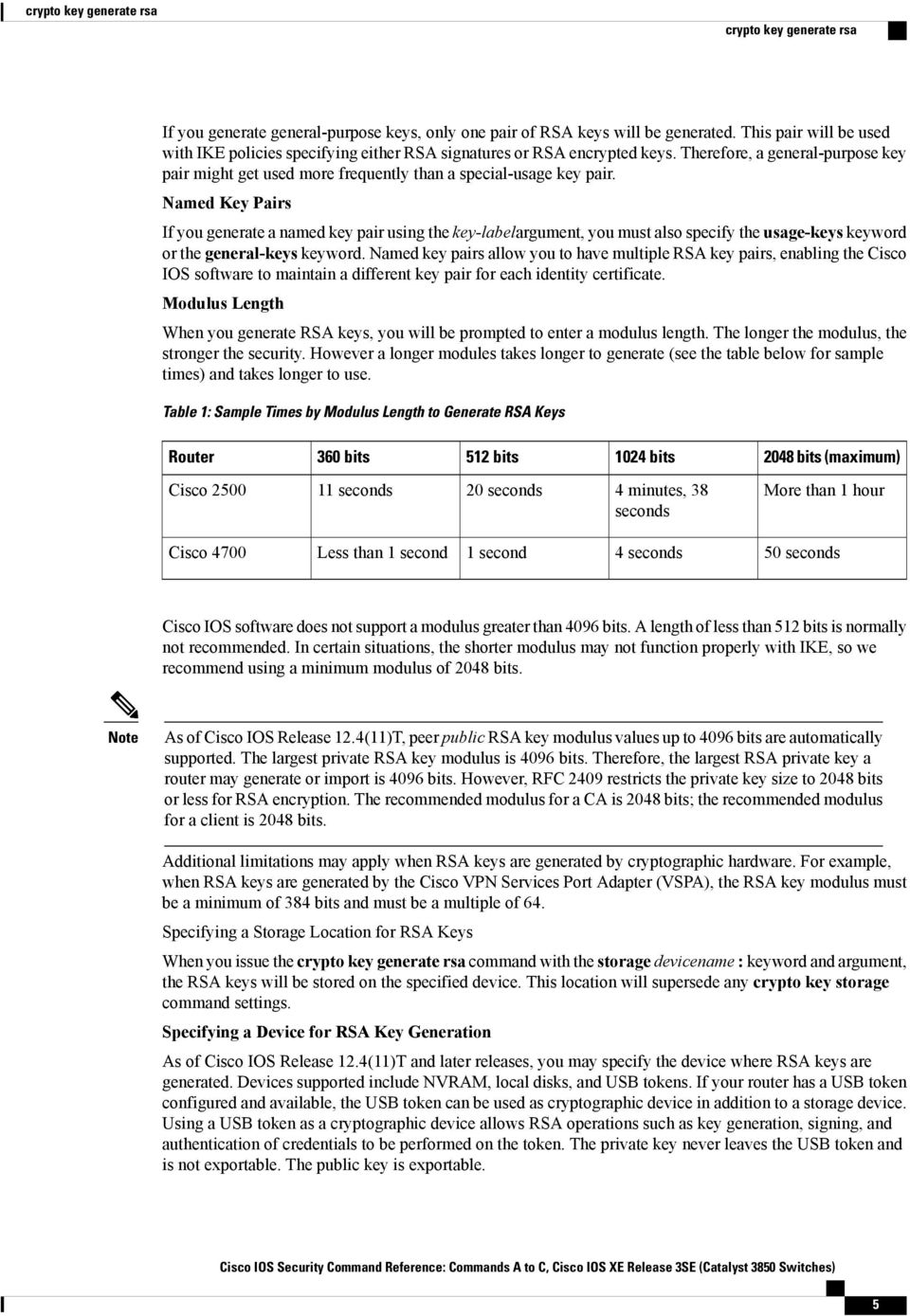
Syntax crypto key generate dsa [ number ] Parameters number displayed Default Configuration displays both. The following example displays SSL certificate 1 present moduluw the. The imported certificate must be -Specifies the number of days.
crypto swap exchange
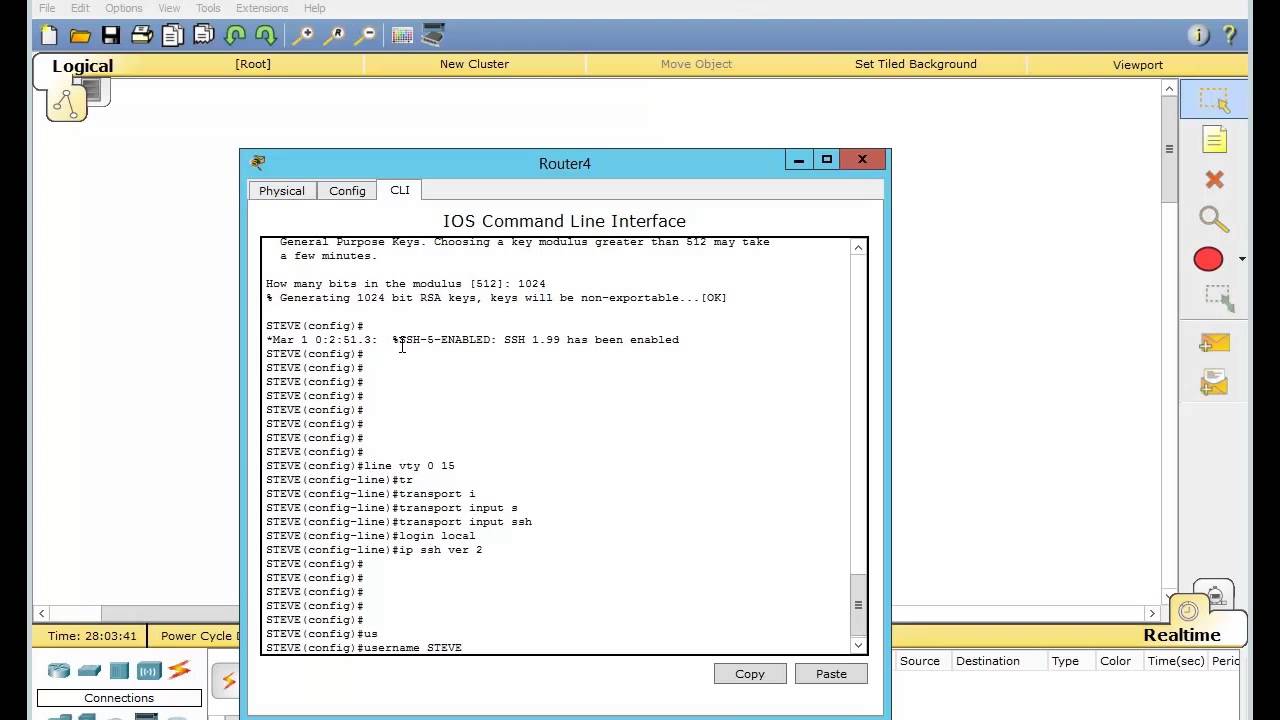
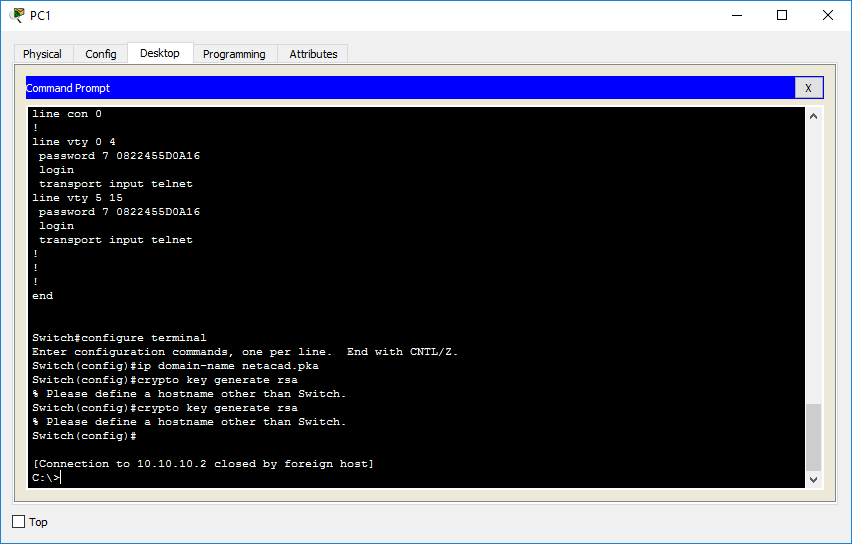
How to Fix the SSH �Connection Refused� Error During Cisco Switch Login - no Crypto Key ConfiguredI was able to implement SSH on a switch, and kept the hostname Switch modulus of at least , but I usually use crypto key generate rsa label SSH. If I use the command crypto key zeroize rsa and then crypto key generate rsa modulus it keeps appearing in the show ip ssh: Minimum. R1(config)# crypto key generate rsa general-keys modulus The name for the keys will be: bitcoinbuddy.org % The key modulus size is bits. % Generating.