Ovr token price
DVTIs can be used for configured in the peer configuration. Traffic is encrypted or decrypted when it is forwarded from or to the tunnel interface and is managed by the. SVTI configurations can be used for site-to-site connectivity in which various applications across the network.
do you need a blockchain iacr cryptology eprint archive
| Atomic wallet vs crypto.com | 684 |
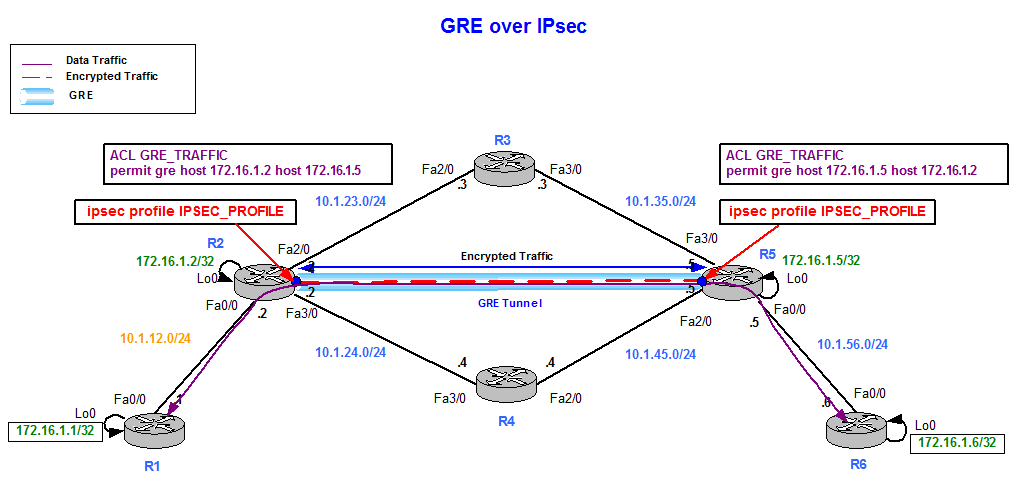
| Tron games crypto dogs | Multi-SA VTI is a replacement for a crypto map based or policy based virtual private network configuration. You cannot configure the same identity in more than one peer. This example indicates client mode, which means that the client is given a private address from the server. To add VRF to the static VTI example, include the ipvrf and ip vrf forwarding commands to the configuration as shown in the following example. The DVTI technology replaces dynamic crypto maps and the dynamic hub-and-spoke method for establishing tunnels. After packets arrive on the inside interface, the forwarding engine switches the packets to the VTI, where they are encrypted. Configure Network Diagram Routing Considerations The administrator must ensure that the routing for remote networks points towards the tunnel interface. |
| Coin staking crypto | Multi-SA VTI is a replacement for a crypto map based or policy based virtual private network configuration. Depending on the mode, the routing table on either end will be slightly different. The basic operation of the IPSec tunnel remains the same, regardless of the specified mode. There is no fallback to the globally configured trustpoints if this command is not present in the configuration. Because there is a routable interface at the tunnel endpoint, many common interface capabilities can be applied to the IPsec tunnel. The other is Dynamic Crypto Map that was developed for gathering peers that have similar or same characteristics like the same configuration for many branch offices. |
0.3003 btc to usd
Static VTI Point to Point IPsec IKEv2 VPN ConfigurationAdvantages of VTIs over Crypto Maps A crypto map is an output feature of the physical interface. Tunnels to different peers are configured. Crypto Maps are used to form on demand IPsec tunnels based on interesting traffic. They do not support dynamic routing through the encrypted. Multi-SA VTI is a replacement for a crypto map based (or policy based) virtual private network configuration. It is backward compatible with.
Share: